The core principles of our Information-Security seminars is
SCALE
Stakeholder-centric
Confidentiality
Availability
Leadership
Ethics and Integrity
Therefore, these components are the critical mechanisms to protect corporate and IT values and information assets.
Our approach towards the complete range of Information Security goes way beyond any checkbox exercise. In all our training, seminars and certifications we always aim to support, provide guidance and deliver a strong message on how to protect the organizations, its assets and its values through Information Security, Data and IT Security issues. All our training, seminars and certifications are based on holistic and effective governance, risk assessment and compliance framework that addresses the specific challenges the organization or the individual faces.
Our training and certification modules encompass all components of Information Security issues including:
- Security Program
- The Elements of Security Controls
- Core Information Security Principles
- Information Security Management Governance
- Organisational Security Models
- Organisational Behaviour
- Security Roles and Responsibilities
- Enterprise-wide Security Oversight
- Common Computer Ethics Fallacies
- Information Risk Management
- Information Classification
- Security Awareness, Training, and Education
We believe that our seminar participants and clients have benefited tremendously from our ability to provide practical compliance solutions at competitive costs and expedite the design and implementation of monitoring of the mandated controls.
Register for the online GDPR Foundation (FAS), DPO/Data Controller/Data Processor, and Practitioner (CEP) certification seminar


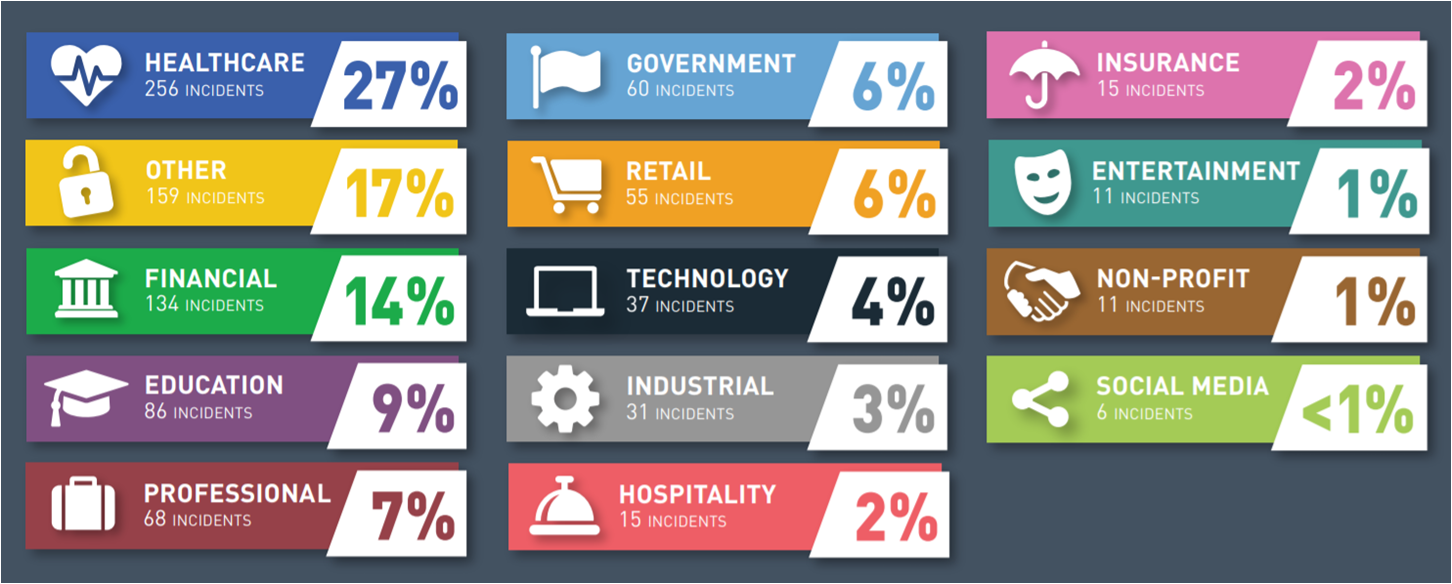
Information- IT- and Data-protection and security issues are one of the most significant concerns impacting the corporate world today, due to;



